Credit Card Payment Processing: What You Need To Know
Posted July 20, 2022 by Jennifer G
The act of paying for something with a credit card is seamless. First, swipe or insert a card into a machine. Then, wait for the authorization to happen. Lastly, sign off on the purchase, if needed. All of this happens in a few seconds.
However, a lot goes on behind the scenes while you’re waiting for that quick authorization! We’ll discuss what happens when you enter your card, in addition to the security measures that are in place to protect your data long after you make a purchase.
Who takes part in the credit card payment process?
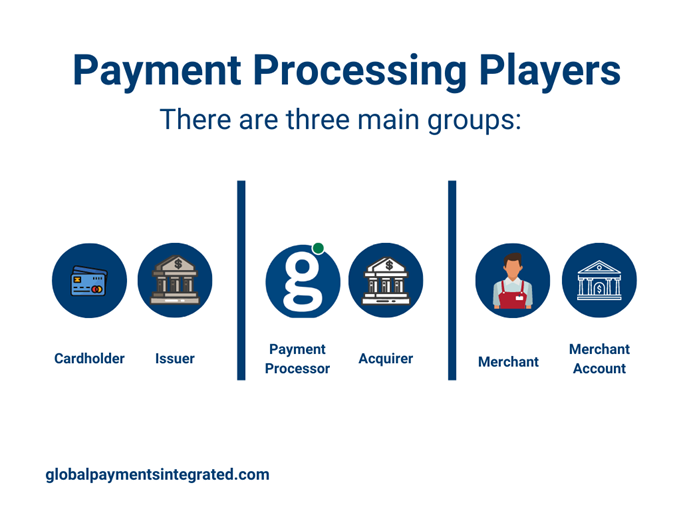
The players involved in the payment process include:
Cardholder: This is the customer that presents their card for payment of goods or services.
Issuer: The issuer (or “issuing bank”) provides the cardholder with their credit and a physical card. They are responsible for approving and declining transactions, customer billing, and collections.
Merchant: This is the business that sells goods or services.
Merchant Account: This is a type of bank account that allows businesses to accept credit, debit, and mobile payments.
Acquirer: An acquirer (or “acquiring bank”) solicits, underwrites, and owns the accounts merchants need to accept credit cards. They can provide the technology permitting businesses to process transactions, take on chargeback risk, and deposit funds into a merchant’s bank account.
Payment Processor: Payment processors are organizations that partner with acquirers to open merchant accounts, handle support, manage payment processing, and build technology on behalf of acquirers.
Facilitating the payment process
Credit Card Machines
First, a credit card reader or terminal is needed. Today, there are various credit card machines available that can cater to any processing environment.
Popular devices include point-of-sale (POS) terminals, which support credit cards with magnetic stripes and chips. Some are magnetic stripe (“magstripe”) only, in addition to devices specially made for an unattended or kiosk type of environment.
Near-field communication (NFC) readers are payment terminals that allow tap-to-pay capabilities for contactless credit cards and mobile wallets.
Payment Methods
The payment transaction starts when the cardholder presents one of the following:
EMV chip card: A payment card containing a computer chip that can validate personal identification numbers (PINs), authorize purchases, verify account balances, and store personal records. Chip cards facilitate EMV® payment processing throughout Europe and the US.
Contactless card: A credit or debit card that does not require physical contact between the card and the credit card machine.
Digital wallet: Digital wallets store a cardholder’s payment information on a mobile app or smartphone device, enabling payment to happen without a physical credit card. Examples include Samsung Pay®, Apple Pay®, Google PayTM, and Fitbit PayTM.
How does credit card processing work?
Once the card is entered into or “tapped” on the credit card machine, the authorization begins. Authorization is the process where the issuer approves or declines a transaction. Merchants use it to ensure customers have sufficient funds available when they purchase something.
- The credit card information enters a payment gateway, which serves as a connector between the merchant and a payment processor (like Global Payments).
- The payment processor will take this information and send it to the card brand (such as Visa or Mastercard).
- The card brand sends this information to the issuer.
When the issuer receives the cardholder’s information, authentication begins.
- The issuer will verify that the cardholder has sufficient funds in the credit line to approve the transaction.
- They may also check the card verification value (CVV) and ensure the billing address matches what is on file to prevent fraud.
- If the transaction is approved, the merchant receives authorization, and the issuer places a hold for the amount of the purchase on the customer’s account. The card reader or POS terminal should see a message that says, “Approved.”
- The merchant gives the cardholder a receipt at the end of the sale.
At this point, the payment verification process is complete.
How long does a credit card payment take to process?
Payment verification only takes a few seconds at the point of sale. Then, the payment process continues behind the scenes with the settlement process.
- Merchants send all approved transactions to the acquirer at the end of the day. This group of transactions is called a batch.
- The payment processor routes the batch to the card branch for settlement.
- The card brand forwards the transactions to the issuer.
- The issuer transfers the funds to the acquirer, and in the process, takes an interchange. Card brands set the interchange fee, and the acquirer is responsible for paying this fee to the issuer.
- The acquirer credits the merchant’s account with the approved transactions.
- The issuer posts the transaction on the cardholder’s account. The cardholder will be responsible for settling their debt at the end of their billing cycle.
Payment processing times vary, but on average, it takes one to three days. Additionally, batches sent during the weekend or a bank holiday get processed on the next business day.
How does a refund on a credit card work?
Even if a transaction is approved, a cardholder can dispute it for a refund post-purchase. These disputes are called chargebacks. The main reasons for chargebacks include fraud, receiving faulty goods or services, and technical errors, such as double charges. A successful chargeback would mean the return of funds to the cardholder.
Check out our chargebacks guide for more information.
How do online payment methods stay secure?
The card payment industry has standards in place to protect cardholder information should a security breach occur. The Payment Card Industry Data Security Standard (PCI-DSS) lays out the minimum security features needed to limit the chances of compromised data.
Encryption is one way to protect cardholder data. With laws becoming more stringent over time, in addition to increasing cybersecurity threats, encryption uses a numeric binary code to shield sensitive data such as the cardholder’s name, account number, expiration date, and service code. The more random the encryption code is, the more difficult it is for hackers to gain access.
Tokenization is another way of protecting cardholder data, particularly the cardholder’s account number. During an online transmission, a token replaces the account number with a unique string of characters. Tokenization differs from encryption in that each token is original and can apply only to a specific merchant and cardholder.
Finding the best payment processor
Now that you understand how complex the payment process can be, it’s essential to choose a processor that will enhance your business.
A reliable payment processor will integrate with your software to provide a seamless checkout and bookkeeping experience for your clients. Additionally, they will enhance cardholder data protection by helping you and your customers stay PCI compliant, ensuring secure payments every time.
Contact us to learn how our solution can benefit your business and add value to your software.
EMV® is a registered trademark or trademark of EMVCo LLC in the United States and other countries. www.emvco.com.
Apple Pay® is a trademark of Apple, Inc. All trademarks contained herein are the sole and exclusive property of their respective owners.
Google PayTM is a trademark of Google, Inc. All trademarks contained herein are the sole and exclusive property of their respective owners. Any such use of those marks without the express written permission of their owner is prohibited.
Samsung Pay® is a registered trademark of Samsung Electronics Co., Ltd.
FitBit PayTM is a registered trademark of Fitbit, Inc. and/or its affiliates in the United States and other countries.
Originally published at https://www.globalpaymentsintegrated.com.


 Subscribe
Subscribe Subscribe
Subscribe



